Warning: Trying to access array offset on value of type bool in /home/smarteduverse.com/blog.smarteduverse.com/wp-content/plugins/sitespeaker-widget/sitespeaker.php on line 13
Blockchain is a type of distributed ledger technology in which different nodes record transactions and reach consensus on a shared state without the use of a centralized authority. The term blockchain refers to a certain form of data structure in which each “block” represents a collection of digital transactions and the “chain” refers to how each “block” is linked to ensure that transactions are recorded in a precise, unchanging order.
A blockchain “network” is a decentralized database made up of a network of computers or devices that agree on a single version of a shared ledger. In a permissionless, public blockchain like Bitcoin, the blockchain network might be made up of thousands, if not millions, of computers or devices acting as nodes. Only a few trusted nodes would operate a network between enterprises in a permissioned chain.
What is a blockchain transaction?
What distinguishes blockchain from other online transaction types is that the data is copied, saved, and confirmed among multiple nodes rather than being held by a single central authority. When a user requests a transaction, the specifics of that transaction are broadcast to all of those nodes in a peer-to-peer method. This prevents anyone from halting or censoring the transactions of specific individuals. Each node then verifies the transaction’s validity and communicates with one another to determine whether the transaction is confirmed.
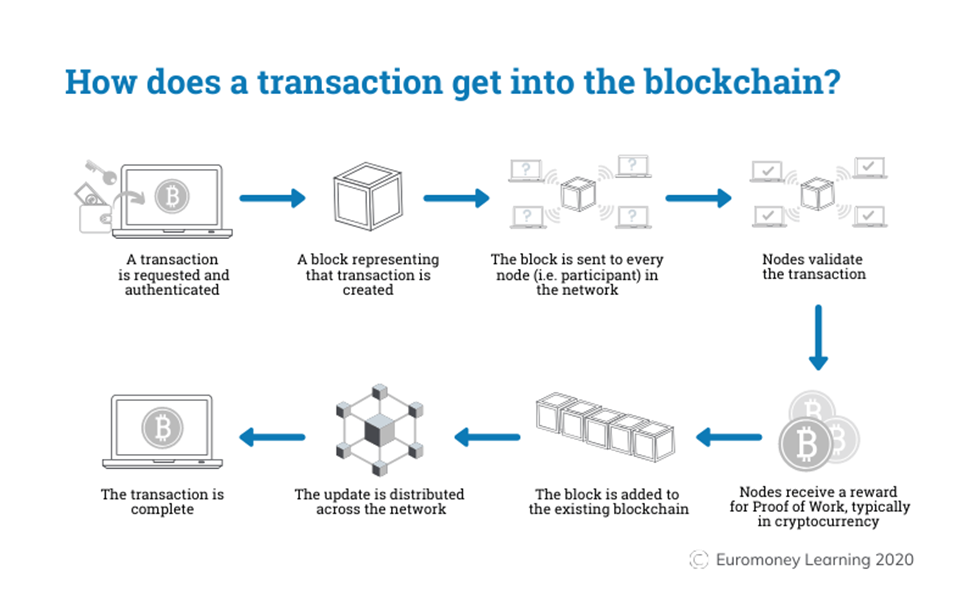
Once validated, the transaction is visible and permanent, and any user of the system can query these transactions at any time, removing the need to rely on a central authority (such as a credit card processor or bank).
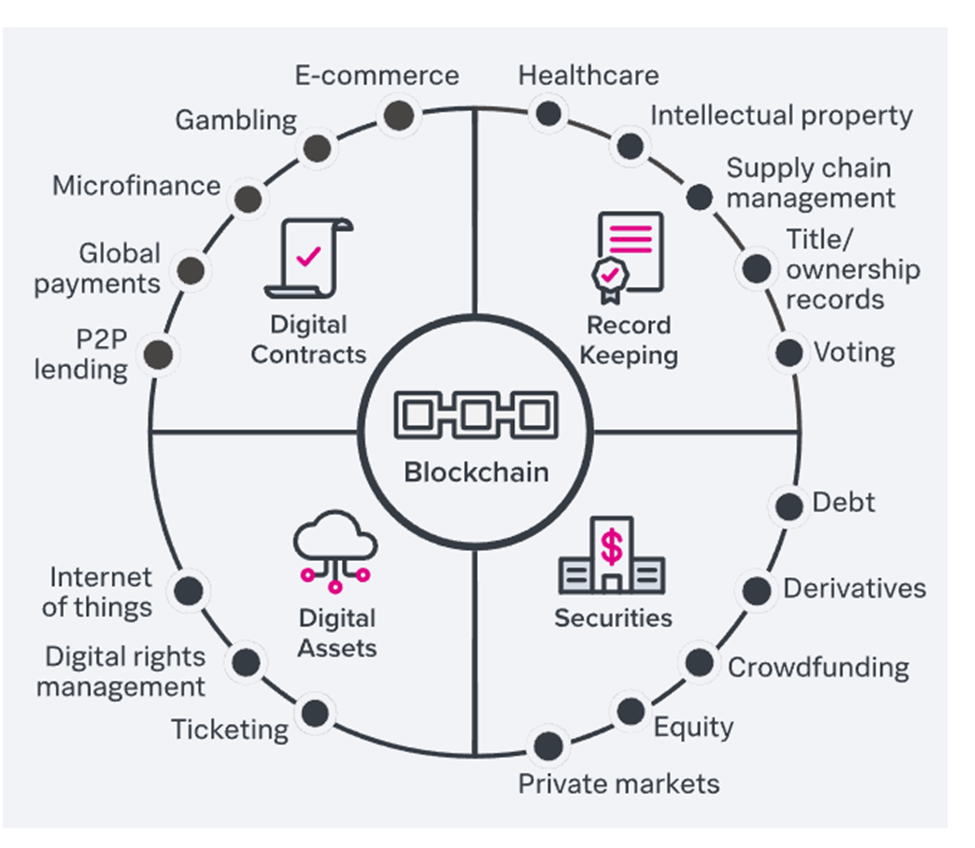
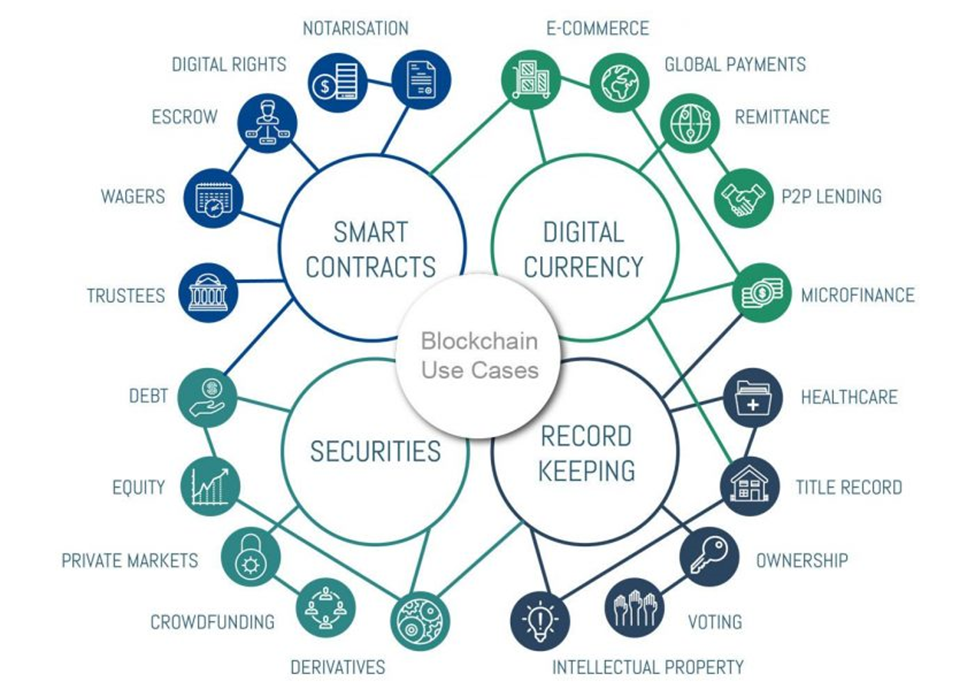
Blockchain transactions are not restricted to the transfer of digital currency (such as Bitcoin); smart contracts enable unique applications of blockchain technology (also called distributed applications or DApps). These smart contracts can help with a variety of transactions, including domain name registries, asset exchanges, lending, insurance, gambling, and social networks, to mention a few.
How does blockchain work?
The blockchain procedure begins with an online transaction suggested to move digital currency between two parties or to trigger the execution of a smart contract. That transaction is subsequently sent as a request to all nodes in that blockchain’s peer network, each of which possesses a complete copy of the digital ledger the entire blockchain’s transaction history. Then, in accordance with the blockchain network’s protocol rules, one node proposes a new block comprised of these transactions, and the rest of the network confirms that the proposed block follows the network rules.
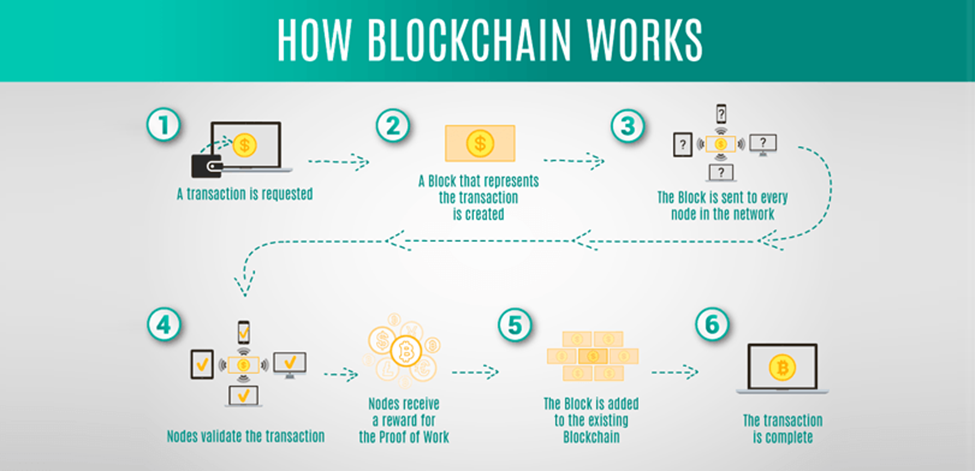
What is the purpose of blockchain?
Above all, blockchain serves as a tool for business security and accountability. A blockchain cannot be controlled by a single entity in terms of security since blocks of information are stored on and validated by various devices across the network. Changing any information would necessitate overriding the entire blockchain network, which is comprised of numerous devices and predefined regulations. Data tampering is effectively rendered impossible. Furthermore, because blockchain technology is distributed, there is no single point of failure, so the network is less likely to experience outages. If a failure occurs, each device has a complete copy of the blockchain, ensuring that data is never lost.
Furthermore, blockchain creates an undeniable, unchangeable record of data that is secure and private, as well as one that has been confirmed across the network. That information can assist firms in ensuring compliance with certain regulatory standards or industry-specific rules, and it can be essential if the organization is subjected to an audit or lawsuit.
How does blockchain technology provide data integrity?
This is where blockchain may help with data authentication. When you attempt to modify a blockchain or change a single piece of data, you produce a new block that must be confirmed by all of the devices in the blockchain network. The problematic data, whether intentionally or unintentionally introduced, will be detected and invalidated before anyone can utilize it.
In an age of growing cybersecurity breaches, blockchain authentication could be extremely useful. In fact, data manipulation has emerged as a major threat. Consider a hacker or a disgruntled former employee infiltrating your network and tampering with accounting data to the point that you can no longer rely on it. Worse, those changes may go unreported, causing you to make vital judgments based on incorrect information. Even an honest mistake in data modification can dramatically harm a firm.